I have been playing with TryHackMea lot, as I prepare for a Security+ exam and try to round out my IT education. In doing so, one of the access options you have is connecting from a Kali Linux box. Although I've certainly dabbled with Linux systems, I've yet to employ Kali (traditionally known for hacking/pentesting/dark arts) so I decided to give a go this evening.... in Azure.
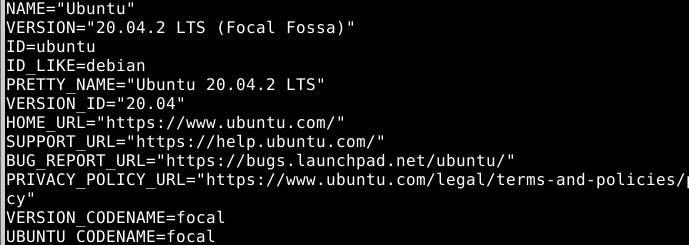 Turns out you can deploy a VM with Kali Linux.. with an OS named desktop-linux-kali, running on v 20 of Ubuntu. I decided to stir the box up from Azure GUIs, first creating a resource from an existing subscription, then preparing storage and setting it up for ssh-entry.
Turns out you can deploy a VM with Kali Linux.. with an OS named desktop-linux-kali, running on v 20 of Ubuntu. I decided to stir the box up from Azure GUIs, first creating a resource from an existing subscription, then preparing storage and setting it up for ssh-entry.
This essentially means you save your private key (which will only show up once, so pay attention) and you use that directory to log in from CLI, or however later. This came in handy for me, later, when I used it to log in and for my root user. Then I used RDC to actually log in, with that username and password. Before I could get this initiated, I did have to enable the port access in CLI, which is a Google-away, & can be done from the Azure CLI/Bash or the interface in Azure.
 While I was ssh-d in from my Windows laptop, I created a new user and a password, just because that's something I like to play around with now. Then it was off to the races.
While I was ssh-d in from my Windows laptop, I created a new user and a password, just because that's something I like to play around with now. Then it was off to the races.
Azure will give you a public IP and you can sign in with that address, plus your username and password to access your VM from RDC. Your resource should be running before attempting, as that will also prevent you from being able to access the VM.
 I've not yet tried to get in to my THM machines (you're given your own IP address to connect with) through Linux. This was primarily why I wanted to grab a version myself... but the Azure VM didn't contain the basic libraries (nmap) so I ended up using the THM provided Kali environment, anyway!
I've not yet tried to get in to my THM machines (you're given your own IP address to connect with) through Linux. This was primarily why I wanted to grab a version myself... but the Azure VM didn't contain the basic libraries (nmap) so I ended up using the THM provided Kali environment, anyway!